Episode One: Key Goals of Patch & Vulnerability Management
In the debut episode of Decoding NERC CIP & OT Security, Foxguard’s Chris Humphreys joins OT cybersecurity leader Derek Harp to explore the key goals of patch and vulnerability management. Their conversation offers deep insights into the evolving landscape of OT cyber risk, compliance, and operational resilience.
Looking for more context on the topics covered in this episode? Explore related posts from our Decoding NERC CIP & OT Security series:
Asset Identification | OT Patching Solution Challenges | Vulnerability Tools to Simplify Patching | The Virtuous Loop & NERC CIP
Decoding NERC CIP & OT Security Podcast: Episode 1 Transcript
Chris Humphreys: So hello, everyone. Welcome to the very first episode of Foxguard’s, OT cyber security and compliance podcast. I’ll be your host, Chris Humphreys.
I am the lead cyber security solutions architect for utilities for Foxguard. My background previously of relevance is I spent the last fifteen years running a firm called the Anfield Group, which is a cyber security and regulatory compliance consulting firm. But also previous to that, I was the first manager of audits and investigations for NERC CIP for the ERCOT Texas Reliability Entity (TRE) region, and helped chair the national level working group at NERC to kind of build the compliance and audit process that’s in place today for better or worse. Previous to that, I was inside the beltway there at the ground level of little agencies like the Department of Homeland Security when they were starting up doing their cyber security missions. And, uh, it’s kind of interesting coming full circle here.
Today, I’m going to tee up my guest and introduce him before I name him because I’m very honored to have this gentleman as our first guest. I’ve known this gentleman for over a decade now, both working together and advocating for cyber security training and awareness and best practices and leading the effort there in compliance and security, and overall, balancing both.
So, I want to highlight a couple of things about what to expect from our podcast as we go. We’re going to talk about OT cyber security. Yes, we do IT. Yes, everyone knows IT, but the OT side of the house is where we want this to be focused, and Foxguard excels in that. We want to talk about patch management, vulnerability assessments and management, and how to implement best practices in OT cyber security and align those with compliance and regulatory standards like NERC CIP. In the future, we’re going to talk about things like cyber security in the cloud, uh, managing vulnerabilities and legacy systems and how to, again, constantly stay strong on compliance while being secure.
Chris Humphreys: First off, a little bit about Foxguard if you haven’t you heard of us.
We specialize in providing comprehensive patch management and vulnerability solutions to OT environments, helping organizations improve their risk posture and achieve NERC CIP compliance. That’s in our utility space. We have a huge presence in the nuclear space as well. Our core offerings are a list of solutions. We have Foxguard Discover, which is our passive OT asset discovery and threat detection. Our platform for Cyberwatch is Compliance, and Vulnerability and Asset Management. We have the Patchintel platform which streamlines OT Patch Intelligence and Acquisition. We have Deploy, where we deploy manual and automatic patch distribution and deployment. We also have a full range of services from risk assessments, program development, audit prep, training, system hardening, patch management as a service and vulnerability management as a service and dedicated OEM services. Obviously, we specialize in compliance and regulation, NIST, NERC CIP, NEI, NIST-2, and many others.
We got our start, which was interesting, years ago as a compute company, which we’re still doing, providing custom computing services, platforms and racks for mission critical industries like energy, aerospace and manufacturing. GE was (and is still) our biggest customer and what started Foxguard way back in the eighties.
We’re going to focus on something called a Virtuous Loop which we’ll get into a little bit later. It’s the visual graphic for our entire approach which ensures continuous improvement in patch management and vulnerability remediation, minimizing risk and downtime. It’s a figure eight and we’ll get into that a little bit later, where security and compliance meet, ensuring constant maturity as you follow this loop.
Chris Humphreys: So, let’s get to our guest. Our guest, I’ve known, like I said, I’ve known this gentleman for over a decade. We worked together at SANS and developed some of the early training for utilities around NERC CIP. This gentleman is a cyber security serial entrepreneur with over twenty-five years of experience. He’s the founder and chairman of the Control Systems Cyber Security Association International (CS2AI), which I learned is pronounced “Ceesay” and is a non-profit supporting over 40,000 OT and ICS professionals globally. He’s co-founder of LogiKeep, Inc, co-invented IntelliShield™, a pioneering IT security product later acquired by Cisco, co-founder of NexDefense, Inc, and now part of Dragos. He is founding chair of the Global Industrial Cyber Security Professional Certification at the SANS Institute and a speaker all over the place. He’s a fellow U.S. Navy veteran like myself, a huge, huge Cub Scout PAC leader of over 150 children, resides in Atlanta, Georgia with his wife and two sons. Ladies and gentlemen, it’s the man, the myth, the legend, Mr. Derek Harp.
Derek Harp: Oh, wow. I think about all the podcasts I’ve done as the host and now I’m getting introduced by you, instead of the other way around. That was fun to be on the receiving end of that. Very flattering. Thank you, Chris.
Chris Humphreys: No, it’s an honor to have you here. And, like I said, Derek and I, I mean, I was so stoked to hear Derek was going to be our first guest and, you know, because Derek and I’ve had a great dynamic over the years, speaking the same languages and advocating for this outreach training awareness and certification route for all of our OT professionals in the industry. And again, I go back to over a decade ago of our late great friend, Mike Assante, bringing me to SANS to help develop the first securing the utility curriculum for the SANS Institute and Derek was instrumental in helping guide me through that and advocating for that. We had some very good times putting that train together, and that education and awareness became a huge passion project of us both but. Derek inspired me a lot in that area. So I thank you for that.
Derek Harp: Well, Mike brought me there too. You know, Mike and I served in the Navy together and formed the LogiKeep IntelliShield™ product. That was Mike and I collaborating many twenty-seven years ago, and yeah, the introduction to OT came by the same person.
Chris Humphreys: And I remember, you know, constantly giving me crap because I’m army intelligence and not navy intelligence. I always said the bar was set a lot lower for army intelligence, but we all did a lot of the same things together. It was always great.
Chris Humphreys: But yeah, so Derek, with your deep OT security expertise and over a decade leading CS2AI – now, again, it is extremely clever how you say that with the abbreviation and acronym, it’s got to be the acronym of the year so far, as CS2AI is pronounced “Ceesay” – you’ve had a front row seat to the ever evolving challenges in the industry.
We want to dive into some strategies a little bit, but I just want to kind of look back a little bit, you know, what are sort of some of the biggest challenges organizations face today in maintaining strong OT security and compliance, just at a high level? What are some of the challenges you see the most?
Derek Harp: Yeah, you know, the first answer to that question, which is fundamentally a great question, like, what are the top challenges? It starts to hint at things like prioritization, but there are so many challenges. What are the big ones? Because maybe we can’t fix all of these, and I know we’ll end up talking on that, but prioritization is huge, and if I had to boil that down real quick, I’d say it’s human being based issues. There are technological things we need to solve, but often that’s about equipping human beings better.
So I ended up looking at everything through the human lens and certainly the CS2AI journey of the last ten years has really focused me on this. And I could think of previous startups that I’ve been involved with, and if I had to be honest, if I went back in time and we gave the technology to a bunch of customers, they couldn’t have operationalized it. You know, we’ve got People, Processes, and Technology (PPT) and holy crap, what we don’t have is bodies, people, but it’s also that they don’t know what to do and they’re not trained right or equipped right. You could give them technology and maybe that won’t work. Now, I think technology can be a great enabler if you don’t have enough people and you need to start training some people who maybe aren’t experts in the space, but they’re going to come up in their knowledge. Then you need to give them tools that help them take certain steps, right? So, you know, the PPT has to work together, but man, oh man, we’ve certainly got some human being gaps.
Chris Humphreys: Yeah, that PPT, the people processing technology is that three-legged stool that I make the focus of every time I speak to a group and kind of the core visual for everyone balancing, you know, a robust cyber security program. Especially in the OT space. I mean, you can have the greatest tools. You can have the greatest things since sliced bread. But if they’re not implemented right or don’t have the right process controls, or the end users running it don’t know how to use it, you know, it’s always going to fail.
Derek Harp: Yeah, yeah! So, let’s say they’re great, but they’re highly complicated. Then you can only help 2% of the population because they don’t have that expertise, you know, so yeah, it matters.
Chris Humphreys: So, let’s talk about CS2AI for a minute. So, you kind of founded that and started that up and what was the impetus for that? What is the focus around that? You know, it’s always been training and outreach and education awareness with you for your entire career. But what is CS2AI’s focus in that realm?
Derek Harp: Well, CS2AI you know, Chris was an accident. You know, if you look at a lot of the startups, and you know, I’d hate to guess how many hours of business plan writing and Excel modeling, you know, it’s also purposeful, right? This is what we’re going to do and how we’re going to do it. CS2AI did not evolve that way. It evolved with a meeting on a rooftop in Atlanta, uh, with myself and I think just one person, Fred Gordy, who I’ve referenced many, many times in different podcasts and events. I think he’s the alpha person. Um, and then another meeting with thirty or forty people in Atlanta and then Washington DC and then Houston.
So, what was it? It was this idea of, you know what – and it was just shortly after a conference – you know what, most of the people who need to get together in Atlanta (was the original discussion) and talk about OT or ICS or control system related cyber security, they’ve never heard of the couple of conferences that you and I go to, Chris. They’ve never heard of them. And even if they had heard of them, they don’t have the money to ever go to them. But they need to understand this part of their risk in their manufacturing facility or their electric grid, you know, utility company. Let’s just start a discussion group in Atlanta. We’ll meet once a month at night and we’ll talk about this, and we’ll see who comes. And so, for years, just hundreds and thousands and now forty you know, 41,000 plus just kept signing up for those discussion groups.
And so sure along the way we needed to figure out, okay, let’s form a nonprofit and how would we get some sponsorship? There’s some costs we need to cover because we’re administrating so many things and so many people, but at the heart of it then, and I think today, is, can we get the wisdom of a relatively few number of people, people like you that could rightfully be called a unicorn? “I understand lots about cyber security, I understand lots about operating technology, I have domain expertise in more than one domain”, you know, that’s not a huge number of people in the grand scheme of the universe, you know, our, world. So the, the knowledge you guys have, how do we get that to the many? And so that’s, I think, that’s at the heart of what we’ve been doing at CS2AI. Hence, you’ve been a speaker at my events! I mean, you know, that’s why.
Chris Humphreys: You have a very impressive list of fellows that you’ve named there, and it’s a long, long list, but uh, I’m honored to have been named one of your most recent fellows in that. And, I think it’s great. I think the reason I love your efforts and CS2AI’s mission is especially within the bulk electric system with our utility base, because 80% of the utilities of our grid are utilities that are small municipalities and cooperative utilities. The learning curve is very, very steep depending on who you’re talking to and to have these resources out to educate and have folks with the same access to expertise, training, and awareness to build robust people processes and technologies, regardless of their budget or size, is something that resonates heavily with CS2AI. And I think from the bulk electric system user group, especially, I think that your organization benefits them heavily.
Derek Harp: I hope you’re right! And you’re right that thousands – I’ve heard six to nine thousand – small utilities alone, and many of them not even having a person with cyber security in their title at all, don’t even have somebody at that location that that’s their job. They’re not big enough to have a person dedicated to it. How do they get what they need? And they don’t go – even if it’s out there – (and it is), and buy expensive training, it’s not in their budget. So, I think that is part of our mandate, why we’ve kept our Wednesdays at one o’clock events, free. Um, you know, we ask sponsors to step up, you know, we got to obviously, um, cover all the costs of doing all this, but, for ten years now, we’ve never charged to come to a Wednesday event and learn, from people just like you. And they’re super well attended, as you know, and the question asking is very intense. And I think it’s because of what you just said; it’s like people starved for various kinds of information and knowledge and networking and peer, you know, access to experts. We try to do all that for them as best we can.
Chris Humphreys: I say this to people and they find it shocking, but I’ve been to utilities where the IT lead SME there started out as the janitor. From a resource standpoint, that’s where you see how strapped these utilities are for expertise and they train from within, and that’s great. But that’s where organizations like yourselves and this training and awareness, and access to great minds like your organization has, make that palpable and digestible for them. It speaks volumes. It really does.
Chris Humphreys: I want to come back to some of the challenges we talked about earlier. One of the things I see the most is, you have to know what’s in your environment. I see organizations, how do they typically approach asset inventory and vulnerability management and where do they often fall short? With my background as an auditor, it was like blood in the water for an auditor when somebody wanted to brag about how robust and locked down their inventory is and how they know everything that’s on there. And then I can easily bring up an open source, you know, tool like Shodan and find their IP address to their EMS system right there in the public domain. You know, I always enjoy things like that, but what do you see in that arena specific to that topic? Like, what challenges do you see? How do you know what’s in your environment first?
Derek Harp: Well, I mean, in that list of, you know, what are the top challenges, I just talked about the human being challenge. If we say, okay, let’s get more granular – asset discovery, asset inventory, where’s all my stuff? You know, it’s pretty much ubiquitous. I don’t care what kind of organization people are wrestling with that. There are those that occasionally feel they’ve got a good handle on it, and there’s mostly those that are honest and say, we’re going to use compensating controls because we don’t know where it all is. So, we’re going to say this is in this enclave, you know, that’s where network segmentation is another big challenge and it’s a huge priority.
You know, our annual report is now eighty-eight pages last year, it gets bigger every year and we see people’s priority in rankings, it’s a downloadable report, free, again, sponsors are underwriting it, and Foxguard is one of our sponsors, which we are so grateful for partnering with you guys. The annual report is a free knowledge product, it’s not a sales job. It’s got huge knowledge in it and it shows those priorities. Where is asset discovery? It’s high on the list. Where is network segmentation? It’s high on the list. So, people are wrestling with that across the world and across companies. I’ve been in major installations where they said, “yeah, don’t ever publicly say this, but yeah, we don’t know where all the assets are and how they’re communicating, now we get into network visibility: we don’t know”.
Chris Humphreys: And then you can’t segue to vulnerability management if you don’t know what you’re protecting in the first place, right? So, you know, we’re worried about vulnerabilities, we’ve got all these vulnerabilities out there, but they don’t even have a solid knowledge yet of what’s in their environment and how to manage that inventory. We see that often, especially on the OT side.
Chris Humphreys: Let’s jump to something a little near and dear to my heart and it’s the kind of, uh, the gospel that I’ve preached for the last fifteen to twenty years, which is, how to balance compliance and security, and specifically, what role does compliance play in shaping vulnerability management strategies?
You know my take has always been, by the time it gets to a compliance regulation, the threat has long since evolved, because of our process to develop these standards, especially in the NERC CIP world. But it does provide a solid floor. It’s not the ceiling of a robust OT cyber security strategy. What are your thoughts on that?
Derek Harp: You know, compliance comes up in so many of our presentations and meetings, and our recent conference that we’re now also doing, you know, the Level Zero conference. And of course, it matters, you know, industry to industry, right? There are plenty of industries, most, not having to comply with anything yet. And then you have emerging compliance. Now NERC and the critical infrastructure protection regulation NERC CIP, that is probably the longest standing addition to this, I mean, what is that? It was born out of the 2003 blackout, right?
Chris Humphreys: Right, and I was responsible for that, version one to version five migration and, you know, coming out of The Department of Homeland Security where we stood up the United States Computer Agency Response Team and the National Infrastructure Coordinating Center, these are the functions that eventually became CISA that we have today, you know, then coming to a place like Texas where I’m going to utilities where they have to go to a board to get authorization to pay for a box of pens. You know, that learning curve was huge and it still is a battle to this day because, those utilities can barely sustain being compliant, much less doing more than being secure to go ahead of their compliance. We now have a lot of data though to support why we need to be more proactive from a security best practices perspective where NERC CIP should be the floor, but not the ceiling, and how to foster a palatable evolution and maturity within organizations of all sizes from a utility base. Um, we see that a lot and I think that’s going to continue to be sort of… I’d like to think we’re getting folks looking more proactively from a security perspective versus just measuring their security bar compliance.
Derek Harp: You’ve nailed a couple of the big themes that are why it comes up all the time. Does compliance equal security? And of course, anybody that knows anything says, uh, you know, being secure or whatever, arriving at some end state – no, it doesn’t. Now there’s people who would also like to say, uh, you know, having to comply with something is overly meddlesome and it’s, you know, a negative situation for them. Well, healthy tension is probably what we need because some of you won’t take any action unless you have to. So, can it be overdone? Yes. Can it be underdone? You know, I manufacture widget ‘A’ and I’m under no, there’s nothing I have to comply with and where’s my maturity? It might be rather low today. If I haven’t had an incident, and I don’t have to comply with anything. So, I’m all for healthy tensions, which means regulations you know, that are very thoughtfully put together, which would mean not just government, sorry, not just government individuals put it together, but a public private partnership to say, what is this thoughtful threshold – and to your point – exceed this. This says don’t be below this, that’s so immature, that’s not okay; be above it. You should have other strategies and other plans, potentially for some of you to be well above it: but be above it. This is a threshold.
Chris Humphreys: Right. And we see all the time, which I don’t understand, what the media’s access is to public disclosures of ransomware attacks, but they’ve got their communications people at these entities that are getting hit with that and end up in the press. They’re trained very well because the first thing out of their mouth is, they say, “we’re heavily regulated and we’ve been compliant with all of our regulations”, yet they still get hit with things like this. At the end of the day, your customers – in an electric utility sense – are without power. You can blame whatever you want, but at the end of the day, customer confidence falls back on that utility, and I think it’s a difficult thing to say, “yes, but I was compliant” and pass the buck to the regulator. At the end of the day, the customer base and our ability to keep the grid up, fall short by pointing fingers. So my philosophy has always been: if you’re secure first, that should produce the byproducts that satisfy compliance. Compliance should never dictate your security model, it’s a foundational layer, but it’s not the ceiling.
Derek Harp: If it’s not balanced right, there’s sometimes things that’ll show up. Now, NERC CIP’s gone through some major reviews a couple times, you know, I remember in different years, like, to fix some ambiguity and to fix some things. It’s not a perfect science coming up with these, you know it better than anybody having been there at the beginning. Sometimes things can sneak in, that really isn’t right to make people… oh, “everybody needs to have, you know, multi-factor authentication on their pipeline process”, well, maybe not. You know, maybe that was waving a magic wand and, you know, “oh, MFA, hey, we’re covered”. Okay, a little more thought needs to go into what you’re making people comply with, but as long as those things are resolved, then, yeah, it can be a good thing to give people sort of a, be above this. You need to be this tall to be on this ride. And so be above this.
Chris Humphreys: So that’s transitions nicely to the importance of having a structured approach in place for OT cyber security, and that’s where I reference this virtuous loop that we’ve come up with. Again, it’s kind of the picture, if you will, the refrigerator poster for Foxguard, and kind of just an overall healthy approach to OT cyber security and maturity.
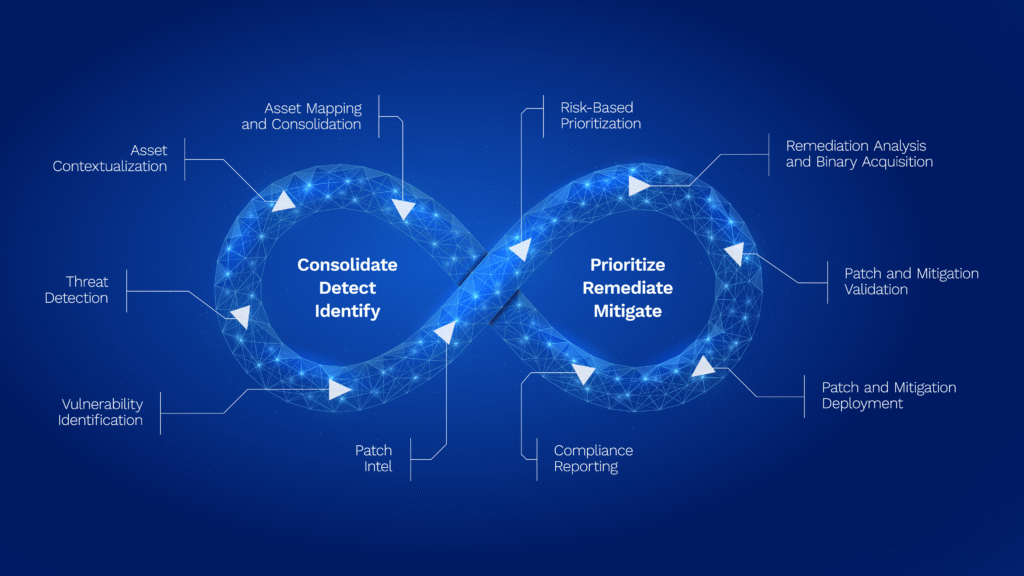
We’ve talked about some key challenges organizations face, but this virtuous loop kind of provides a structural visual, and I want to kind of walk through that very quickly because you’ll see in this loop, you have four key components: identify, prioritize, remediate, and mitigate at the center of the loop, which if any of my NIST CSF fans are out there, the cyber security framework, you’ll notice those four components are control families from the NIST CSF. So, there’s your security focus. But then as you go around this loop, you have asset mapping and consolidation, asset contextualization, threat detection, vulnerability identification, patch intel; all that kind of loops around and you can tie the NERC CIP framework to each one of those, as sort of a, “here’s my security based approach mapped to NERC CIP”.
I think that visual – I’m always a fan of a picture is worth a thousand words – whether you’re talking to an executive manager, or whether you’re talking to an engineer, this visual makes it very, very easy to kind of show the flow of maturity while being compliant. I think that’s a huge component of giving that visualization. So again, talking about identifying first what you have, then prioritize and remediate and mitigate the protections around it. It’s very, very simple. When we talk about our solutions at Foxguard that support NERC CIP to that loop, you have CIP-2 with your best cyber system categorization, Cyberwatch is our solution there. We have a list of solutions here that fit into that loop. CIP-7 security patch management aligns with Patchintel, Deploy, and Cyberwatch. What I think is critical about our Patchintel component – and Derek you can relate to this – the credibility that comes from this as far as our role with being awarded DoE funding to develop a patch management solution for the bulk electric system, and this being that same solution, always gives vendors some substantial credibility as trusted advisors, which is what we want to be seen as. We don’t want to be like, we’ve got a product suite that we can sling, we want to solve the problems and these products have come out of those problem sets, and organizations like our national labs and DoE, to get those things done. Um, CIP-10, we have our configuration change management solution that matches to Foxguard Patchintel and Cyberwatch. We have supply chain management for Patchintel and we have CIP-15 which is a new one coming down for internal network security monitoring that our Discover capability has. So, we have a solution set here that aligns with that loop.
But before we close and wrap it all up, let’s talk about in depth the challenges in any OT environment, but in NERC CIP environments especially. We see things like asset diversity, managing and tracking of multiple patch sources, third party vendor approval tracking. Applicability and app evaluation and prioritization, uh, maintenance and window availability, closed loop patch status reporting, all that time and resource availability. Again, the human factor…
Chris Humphreys: We talked about the strategic, let’s talk about the tactical components that are the challenges of maintaining sort of, just in a patch perspective, just talking about patching and vulnerability management. Do you have any insight into that at a high level?
Derek Harp: It’s also a very, very frequent discussion and frequent question for speakers, even if that’s not the core of their, you know they’re one of our talks on our CS2AI platform: it comes up anyway. In one form or another, you know, people are wrestling with it, especially depending on their background. If they’re coming to this community from an IT centric background and they’re used to patch Tuesday, they can be quite frustrated to find that just patching the way we’ve been patching IT systems, you can’t necessarily do that here. We may have a power plant that’s going to be up all year this year, except for six hours in November, you know, that’s it. And it’s not supposed to be down between now and then. And so that’s an extreme example.
We had a manufacturing event recently, you know, I’d heard this already, but one person said, “now we do take lines down”. So unlike maybe utilities that can’t come down, uh, we do know a line is going to be down. Now we need to be very aligned with the operations folks, it’s all pre-piped, so they know when they’re down, and we want to do something then. It’s not like, find out after the fact that, hey, you guys are down! They have work to do. They’re bringing the line down. They have other job accomplishments they need to do. You know, so bottom line is – and it comes up all the time – how do we safely do it? What’s the appropriate way?
Companies like yours, like Foxguard, are working on that answer, which is to say, “hey, there is a better way than what we’ve been doing in OT”, which is a lot of not patch these things and just do compensating controls, and say “inside this enclave is a bunch of unpatched stuff, we’ll just try to reduce access to the area, but we can’t get to those things”. That’s been the answer for a while. I think for a lot of folks. The smarter answer over the future will be green state technology that’s better designed, obviously, to be able to be updated, technologies, you know, and things like the Patchintel type of system, telling you where to focus your time. That’s the way of the future, right? And we will then be able to have – again, not all of these verticals are the same – but in general, we’ll have a better situation of being able to patch. Whereas today the state of the union has been largely, woefully under, you know, unpatched or under patched.
Chris Humphreys: Yeah, and that brings back to, again, for me that I find tangibility with my audiences in the fact that this is, I think, 70% of this problem is a human and administrative challenge. It’s not a technical capability, it’s, you know, corralling all these multiple sources from different areas, you know, getting on the right patch schedule for each of those, and having the right people and processes to sustain that, you know?
I go to, you know, we go to prospects all the time, to utilities, and we talk to that CIO or CISO or director of compliance, and they say, “yeah, our patch management process is extremely mature, nothing’s broke, we’re fine”. But then when I talk to his team of eight people that are eight different people with a control in that process, that’s manually dependent on that person to execute – it’s not mature. It’s not sustainable. So, I think the patch challenges, especially with NERC CIP, I think if we can corral the administrative and human component to it, to make process more efficient, the technology exists! You know, I think the presentation I gave for you guys at your last symposium was, why does CIP-7-R2, which is your patch requirement, continue to be since day one, the most highly violated NERC standard? You know, and I don’t think it has anything to do so much with the technical competency, it has to do with people and processes.
Derek Harp: And like you said, if you don’t know where everything is, you start to think patching what? Right? So, I love the virtuous loop because, the one thing about that, that meshes 100% with my, you know, what I find my core belief today is, and I think many people who really see how all this works; there’s no, we’re not trying to arrive at a destination called ‘secure, we finally made it’, which sounds like these linear lines, like “asset discovery, finally, all this money and time, we’re done, we got it done”. Well, anybody who knows anything says that doesn’t make a whole lot of sense. You got more stuff coming and going and so it’s not, you don’t arrive at any of these. So the concept of it is, can we make progress that we can demonstrate, measure, celebrate (I would suggest) and keep doing that? It’s a process, not a destination. So I think that’s, you know, completely aligned with that, that’s the way it’s got to be.
And maybe you, in a prioritization scheme, you also even rank your assets, you know, this location, in the same company, is different than this location as far as risk, and so do that one, you know? So make things either manageable, use the, you know, the right tools, methods, you know, and tools, then the people you have – who you typically don’t have enough of – then they can do the most important things next. And then they can move on to the next, you know. And so it’s an ongoing process, we have to be committed to it, we’ve welded all these systems together, we want the connectivity, we want the bonuses of it; efficiency, remote controls, you know, all the intelligence about how our operations are working. We want all that. Well, there’s a hidden cost to that. We’re now going to be committed to this loop and this process. There’s no destination we’re going to get to where we’re secure, finally, that’s not a thing.
Chris Humphreys: That brings us to the last topic I want us to kind of highlight on, that is still in the utility space especially. This is a debate that’s, it’s a very front and center debate for folks as far as technology adoption and things like that. It’s around automation, and is automation a friend or a foe? And I think the benefits far outweigh the risk as a whole, but when you have, you know, I have utilities that are on ten-year-old legacy systems because they work. And they can maintain them and they don’t need to, you know, they have a switch yard where they can send an operator out to open and close the breaker still, and it works for them. Um, how do we see that? Is the debate for justifying legacy technology still a relevant one in the world you’re looking at?
Derek Harp: Well, I think I would maybe come at it differently. I like the analogy that automation is a genie, you know, in a bottle and it is out of the bottle. But it depends on what you wish for, right? There’s all the stories and jokes; the genie can go multiple ways. So, to say automation, is it good or is it bad? Well, I guess the answer is yes. It’s all these things, but the genie IS out of the bottle and there’s no putting it back: there’s too much money at stake.
So, I’ve been seeing this unfolding for ten years. I remember a presentation that really focused me on it, and it was around how much money is at stake being able to have data go from a turbine up to a data lake and back to the turbine. Yes, attenuating or adjusting, making a change at the turbine from data coming back from the data lake. You know, people were horrified in the presentation and there’s a major OEM making the presentation and the security, you know, hard hat wearing security dudes were like, this is horrible. They missed how much money he said was at stake per turbine, per plant, per company that has this many of these turbines, millions of dollars. And I looked at that, I wore my entrepreneur business hat and said, that’s going to happen. So it’s a question of how do we do this? So I think the automation genie is out of the bottle. Yes, there are some legacy systems that have some positives to the fact that they are maybe legacy. But, you know, they also have challenges. So I think it’s a case by case basis, asset by asset basis, even within a company, to say, “what are we trying to do here?”
Now, absorbing all or adopting all automation because it’s shiny, we probably shouldn’t do that, but we’re going to adopt this automation and we’re going to look not only at its return on investment—the reason we want it—we’re going to look at its risk and say, okay, we quantify both, we plan to save this much or make this much or whatever the gain is, the reason we’re adopting this automation, and see if the risk is acceptable, or if we’re going to mitigate it to acceptable. And then we’re going to do this automation. So, I think it should be very thoughtful, not just, let’s just keep buying stuff that’s got new whiz bang technology in it.
Chris Humphreys: Right, and that genie better be able to grant more than three wishes, right, when it’s out of the bottle, you know, or one of those wishes better be, uh, “I want infinite wishes”, you know, so the age-old story, yeah.
Well, with that, I think that’s a nice kind of way to end this and wrap this up a little bit.
Derek, I really want to thank you so much for being a part of this. I always love when you and I can get together and talk about these things. I know we could go on forever, but uh, you know, I think our two organizations benefit really well from speaking that same language and carrying that same message. Um, I say spreading the gospel of sound OT security best practices will yield compliance and continue that education and awareness going forward.
I think, um, you know, this is our first episode, uh, Derek, I’d welcome you back anytime, as much as you want, and vice versa. I’d be happy to participate in your organization’s efforts as well. But I think our next episode, we’re going to be doing Patch Management Uncovered: Lessons, Mistakes, and the Path Forward, with focus solely on patch. We have blog topics that are coming out in between those, around NERC CIP and patching. That’s going to be coming forward, look for that, uh, and our Foxguard LinkedIn and our Foxguard outreach.
Um, but Derek, again, I want to thank you so much for being our first guest, and, uh, I just, again, always love being able to talk with you and bounce these ideas and have this debate.
Derek Harp: Hey, I’m honored to be the first guest and yeah, you and I have got lots of things to talk about in the future on the CS2AI platform, the Level Zero conference platform and, uh, on your podcast. Yeah, I welcome all that and I’ve enjoyed all our interactions too over the years and love the Foxguard family and team to be honest. That’s not something I could say ubiquitously for all the partners I have in the world. Uh, you guys are amazing and, you know, it sounds like hype, but the truth is, you’re a wonderful group of human beings that we enjoy interacting with and um, I love that you guys have some portion of who you are dedicated to how we make the universe better. Um, not, not everybody’s got enough of that. I think, you know, we all need to be thinking about that, so thank you for that.
Chris Humphreys: No, I appreciate it, and I think making the universe better is our shared vision and we love to have you as part of that and continue to carry that on. Um, with that, thanks a lot for listening you guys, listeners, if you want to send comments to our LinkedIn page, uh, if you have questions and things you want to see going forward or want to contribute, uh, feel free to post those and we’ll get those incorporated into our, our future content. Thanks a lot, everyone. Have a great day.