Welcome back to our NERC CIP compliance and OT security blog series, where we break down the complexities of compliance for utilities and Independent Power Producers (IPPs) operating in OT environments, In this instalment, we explore the interconnected processes at the heart of NERC CIP compliance, what we call, the “Virtuous Loop.”
Starting with asset identification and mapping, and continuing through threat detection, patch intelligence, and compliance reporting, this blog outlines the cyclical approach that empowers organizations to streamline their compliance efforts and enhance overall cyber security resilience.
We’ll show how Foxguard’s essential toolkit can play a central role in closing the loop, helping ensure no gaps exist between asset awareness, risk assessment, patch management, and compliance validation.
Decoding NERC CIP Series:
Decoding NERC CIP & OT Security podcast: Episode One: Key Goals of Patch & Vulnerability Management.
Asset Identification | OT Patching Solution Challenges | Vulnerability Tools to Simplify Patching
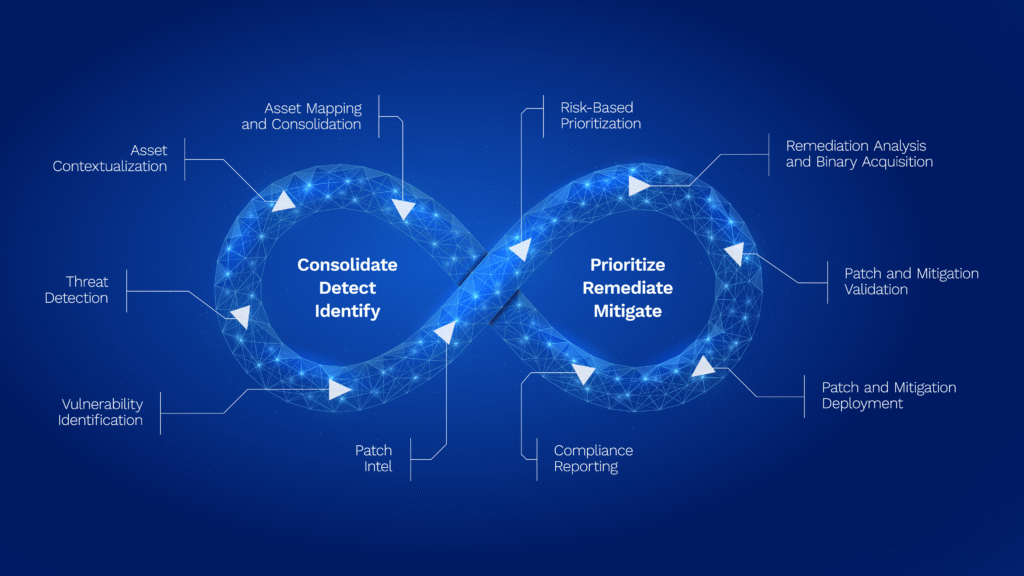
Asset mapping and consolidation
The first step toward NERC CIP compliance in the OT environment of an electric utility or IPP is to identify BES Cyber Assets and group these into BES Cyber Systems by following these steps:
- Using a tool like Foxguard Discover, identify devices that meet the NERC Glossary definition of Cyber Asset (“programmable electronic device”).
- Identify BES Cyber Assets (BCA) in compliance with CIP-002-5.1a Requirement R1 and the NERC definition of BES Cyber Asset: “A Cyber Asset that if rendered unavailable, degraded, or misused would, within 15 minutes of its required operation, mis-operation, or non-operation, adversely impact…the reliable operation of the Bulk Electric System…”
- Consolidate BCAs into BES Cyber Systems (BCS) in compliance with CIP-002-5.1a Requirement R1 and the definition of BES Cyber System: “One or more BES Cyber Assets logically grouped by a responsible entity to perform one or more reliability tasks for a functional entity.”
- Classify BCS as high, medium and low impact, in compliance with CIP-002-5.1a Requirement R1 Parts R1.1, R1.2 and R1.3, and following the criteria in Attachment 1.
Asset contextualization
Other types of systems that are in scope for NERC CIP compliance are discovered through their context, supported by Foxguard Discover and NERC-CIP Services:
- In compliance with CIP-005-7 Requirement R1 Part R1.1, make sure that an Electronic Security Perimeter (ESP) for an asseti has been drawn such that every component of a BES Cyber System (including BES Cyber Assets) that is installed in the asset is included in the ESP.
- In compliance with CIP-005-7 Requirement R1 Part R1.1 and the NERC Glossary definition of Protected Cyber Asset (“one or more Cyber Assets connected using a routable protocol within or on an Electronic Security Perimeter that is not part of the highest impact BES Cyber System within the same Electronic Security Perimeter”), identify any Cyber Asset that is installed within the ESP but is not itself a component of a BES Cyber System as a PCA.
- In compliance with CIP-005-7 Requirement R1 Part R1.2 and the NERC Glossary definition of External Routable Connectivity (“The ability to access a BES Cyber System from a Cyber Asset that is outside of its associated Electronic Security Perimeter via a bi-directional routable protocol connection”), identify all instances of ERC.
- In compliance with CIP-005-7 Requirement R1 Part R1.2 and the NERC Glossary definition of Electronic Access Point (“A Cyber Asset interface on an Electronic Security Perimeter that allows routable communication between Cyber Assets outside an Electronic Security Perimeter and Cyber Assets inside an Electronic Security Perimeter”), identify each Electronic Access Point (EAP) on the ESP.
- In compliance with CIP-005-7 Requirement R1 Part 1.2 and the NERC Glossary definition of Electronic Access Control or Monitoring Systems (“Cyber Assets that perform electronic access control or electronic access monitoring of the Electronic Security Perimeter(s) or BES Cyber Systems…”), identify any Cyber Asset that contains an Electronic Access Point as an EACMS (other Cyber Assets, such as AD servers and some Layer 3 switches, may also meet the EACMS definition).
- In compliance with CIP-005-7 Requirement 2 Part 2.1 and the NERC Glossary definition of Intermediate System (“A Cyber Asset or collection of Cyber Assets performing access control to restrict Interactive Remote Access to only authorized users. The Intermediate System must not be located inside the Electronic Security Perimeter”), identify each Intermediate System installed at the asset.
Threat detection
Customers of Foxguard’s Cyberwatch solution receive immediate, targeted alerts on emerging threats. This ensures rapid response and proactive Cyber Security measures to mitigate risks effectively.
Vulnerability identification
By searching vulnerability databases including the National Vulnerability Database (NVD), Foxguard Cyberwatch identifies newly reported vulnerabilities in software and firmware installed in OT devices in your organization’s environment. Foxguard supplements this information with comprehensive risk details from various sources, including safety agencies, CVE Numbering Authorities (CNAs) and vendors.
From the NVD, Cyberwatch retrieves and displays severity information for the vulnerability, including:
- The values of the variables in the Base Metric Group (components of the CVSS Base Score).
- If any values have been entered into the CVSS Threat, Environmental or Supplemental Metric Groups, these will be retrieved and displayed as well.
Cyberwatch also retrieves and displays exploitability (i.e., likelihood) data for each vulnerability, including:
- From FIRST.org, the EPSS score for the vulnerability.
- From CISA, the presence or absence of the vulnerability in the KEV Catalog.
- Availability of an exploit kit for the vulnerability.
Note: EPSS scores, the NVD, and CVE libraries are updated at least daily in Cyberwatch, ensuring your organization receives timely, accurate, and actionable data for effective vulnerability management.
Patchintel
Foxguard Patchintel provides comprehensive intelligence regarding patches that are available for products used in your organization’s environment. Instead of scouring vendor websites to check for new patches for your assets, you can have the detailed patch information you need to make informed decisions at your fingertips. You can utilize integrated vendor release notes and security bulletin links in our intelligence data to expedite the review and analysis process.
Risk-based prioritization
While the NERC CIP standards don’t require Responsible Entities to identify or manage software vulnerabilities, CIP-013 R1.2.4 requires “Disclosure by vendors of known vulnerabilities related to the products or services provided to the Responsible Entity.” Since a vendor should never disclose a vulnerability without having a patch available, this Requirement Part essentially means vendors of products related to BES Cyber Systems are responsible for identifying, disclosing and patching all vulnerabilities in their products.
The phrase “known vulnerabilities” implies that all vulnerabilities need to be treated equally, no matter how much or how little risk they pose. In other words, the vendor is not empowered to ignore vulnerabilities that don’t pose much risk to their product; they must patch every vulnerability in their product that they know about. Of course, this just exacerbates the problem of patch overload that so many NERC entities are experiencing today.
That problem is further exacerbated by the fact that CIP-007 R2 doesn’t permit the NERC entity to “pick and choose” which patches they want to apply, based on risk mitigated by the patch. If their patch source sends them a patch, they need to apply it, regardless of how much or how little risk it mitigates. In other words, NERC entities subject to CIP-007 R2 compliance are not allowed to prioritize patch applications on their own, while still maintaining full compliance with the letter of CIP-007 R2.
However, since Foxguard’s Patchintel service is its customers’ patch source for many OT software and firmware products, it can address this problem itself. If Foxguard decides a patch doesn’t mitigate enough risk to be worth applying, it can remove that patch from the set that is provided to the customer. Thus, the customer can avoid applying an unnecessary patch, while at the same time maintaining full compliance with CIP-007 R2.
Remediation analysis and binary acquisition
With every patch distributed to customers, Patchintel provides its own analysis of remediation options for the vulnerability or vulnerabilities addressed by the patch. Foxguard also provides remediation options from other sources, including the product supplier itself.
Foxguard lets you acquire patches in two ways: The Patch Acquisition Report (PAR) provides links to all the patches (across all vendors) to which your organization subscribes, while the Patch Binary Acquisition service provides the patch binaries themselves, with assurance of authenticity and integrity.
Patch and mitigation validation
When a NERC entity receives a security patch for an OT product they operate, the first thing they need to do, per CIP-007 Requirement R2 Part 2.2, is determine whether it is in fact applicable to their instance of the product; this is called patch validation. For example, the entity might find that the patch applies to a different version of the product than the one they operate. Or they might discover the patch fixes a vulnerability that only applies to the Windows version of the product, while the entity is running the Linux version.
To make this job easier for the user, Foxguard’s Patchintel and Cyberwatch solutions provide a wide range of information to help a NERC entity determine whether a patch is applicable to an OT product that they utilize, as well as risks that might come with its application. This information includes vendor patch release notes and security bulletins. Foxguard can make this information available to customers in both text and binary form, so it can be utilized by third party asset management tools that their customers may use to determine patch applicability.
If a patch can’t be applied immediately or may never be applied, a mitigation plan needs to be in place. This is for compliance with both OT best practices and CIP-007 Requirement R2 Part 2.3. The supplier of the product often provides mitigation information, which Foxguard will pass on to the user. However, Foxguard also provides mitigation information from other sources, as well as Foxguard itself.
Patch and mitigation deployment
Foxguard Deploy offers flexibility for various deployment models, from single servers to large fleets. You can choose between agentless and agent-based options, with manual, semi-automated, and fully automated patching. You can maintain control over deployment timing, user notifications, system restarts, and optional delays to fit your business requirements.
For cases in which a patch cannot be applied immediately or even at all, Foxguard’s professional services will help you decide on the best mitigation strategy and implement that strategy.
Compliance reporting
Foxguard’s NERC-CIP services, supported by the Cyberwatch platform, help your organization generate the evidence you need to prove compliance with all the Requirement Parts of CIP-007 Requirement R2, including:
- Evidence of identification of a patch source or sources for compliance with Part R2.1.
- Evidence of evaluation of security patches for applicability in Part R2.2.
- Evidence that, for every patch identified as applicable in Part R2.2, your organization, within 35 days, did one of the following:
- Applied the applicable patches;
- Created a dated mitigation plan; or
- Revised an existing mitigation plan.
- Evidence that, for each mitigation plan created or revised in Part 2.3, your organization implemented the plan within the timeframe specified in the plan, unless a revision to the plan or an extension to the timeframe specified in Part 2.3 was approved by the CIP Senior Manager or delegate.
Moving Forward Together
NERC CIP compliance is a continuous cycle of asset awareness, risk assessment, remediation, and documentation. As regulatory demands grow more complex and OT environments become more interconnected, electric utilities and IPPs need to take a more unified approach.By integrating asset discovery, vulnerability management, patch intelligence and deployment, mitigation planning, and compliance reporting into a cohesive ecosystem, Foxguard is purpose-built for this challenge, helping close the loop on NERC CIP compliance.
Whether you’re starting your compliance journey or refining a mature program, our services and expertise are here to support your team every step of the way. With Foxguard, you gain a trusted partner in building a secure, sustainable, and fully auditable compliance process.
Let’s move forward together. Reach out today to learn how Foxguard can help your organization operationalize a smarter, repeatable approach to NERC CIP compliance.