Patching an Operational Technology (OT) environment poses unique challenges that are rarely a concern when patching more traditional IT assets. Those working in OT understand that we operate in a completely different world when it comes to Industrial Control Systems. PLC’s, HMI’s, SCADA systems, relays, switches (no, not that type of switch); our assets are expected to operate 24/7 and taking them offline for patching can have serious operational implications.
Patching may need to be performed during pre-scheduled downtime, or in some cases, it may not be feasible at all. In addition, OT assets have real-world, physical implications. Their 1’s and 0’s could be the difference between a safe shutdown and an explosion; your IT server is unlikely to face the same safety risks. The stakes are higher in OT/ICS, which is why a comprehensive plan is essential to safeguard against potential vulnerabilities in our systems.
So, how can OT professionals determine the best course of action?
This article explores why OT patching is uniquely challenging, breaks down how to prioritize vulnerabilities, and discusses when alternative mitigation strategies might be the better choice. With these strategies and careful planning, organizations can bolster security without disrupting uptime or daily operations.
The Challenges of Patching in OT
Unlike IT environments, where updates are often applied overnight with minimal disruption to operations, OT systems govern critical infrastructure, such as power grids, nuclear plants, and transportation networks. Even a brief downtime in these environments can result in serious operational, safety, or financial consequences.
In OT, patching decisions must be carefully evaluated. While unpatched vulnerabilities pose risks, applying updates without proper planning can also introduce instability. This makes it essential to balance patching with other mitigation strategies to maintain security and system availability.
Given these challenges, what specific factors contribute to the complexity of patching in OT environments?
- Legacy and diverse systems: OT environments are often a patchwork of old and new technologies, with many legacy systems designed long before cyber security was a priority. These systems may lack modern patching capabilities and pose a heightened security risk.
- Vendor dependencies: Unlike IT, where updates are often directly controlled by the organization, OT patch deployment may require vendor approval or intervention. This can lead to delays, especially when systems are highly specialized or when the vendor’s patching schedule doesn’t align with operational needs.
- Availability concerns: Shutting down OT systems, even temporarily, can cause major disruptions to operations, safety, and productivity. While reboots may be acceptable for certain IT environments, many OT assets, especially servers and networking equipment, demand careful coordination to minimize downtime.
- Compliance challenges: Stringent regulations, such as NERC CIP and CISA directives, impose strict mandates on patching processes. Compliance requirements can often delay or dictate how patches are deployed, especially in industries dealing with critical infrastructure.
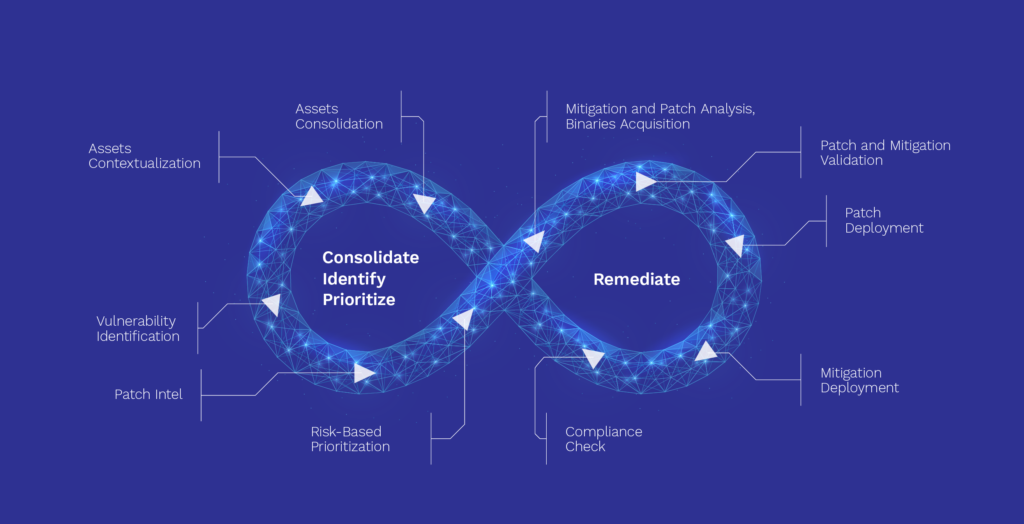
The Virtuous Loop: A Smarter Approach to Patching
In OT environments, patching can’t be a one-time event. Given the complexity and criticality of these systems, organizations need a dynamic strategy that evolves with new threats and shifting operational demands. This is where Foxguard’s Virtuous Loop comes into play— our full-service ecosystem designed to ensure continuous protection without disrupting day-to-day operations.
Picture a factory operating 24/7, where patching can’t be a one-time event, but rather an ongoing, thoughtful process. The Virtuous Loop offers a smarter approach, transforming patch management into a proactive, cyclical process. By integrating security seamlessly into ongoing operations, it addresses vulnerabilities continuously, ensuring both uptime and safety are prioritized.
The Virtuous Loop is a long-term solution, crafted to evolve with your organization’s needs. It provides a dynamic framework that adapts to new threats and business changes. Here’s how it works:
- Identify, Classify & Contextualize Assets: The first step is knowing what you’re protecting. An accurate asset inventory, including classification, helps you pinpoint vulnerabilities before they pose a risk. Without this visibility, it’s impossible to secure your environment.
- Vulnerability Information and Patch Intelligence: Once you’ve identified your assets, the next step is to uncover their vulnerabilities and missing patches. Continuously scanning for security gaps ensures you have the latest intelligence on potential risks.
- Prioritize: Not all vulnerabilities demand the same level of attention. Prioritize based on the potential impact to both security and operations. Context matters: a low-level vulnerability in a critical or exposed system can be more impactful than a severe vulnerability in a non-essential device or a device that is protected by a compensating control.
- Remediate and Mitigate: Sometimes, patching isn’t an option. In those cases, use compensating controls like network segmentation or other mitigation strategies to reduce risk without causing downtime.
- Validate: Develop and maintain a validation strategy, utilizing a dedicated lab environment, early adoption on non-critical systems, and a documented testing strategy to minimize the risk of a patch causing functional or performance issues.
- Evaluate and Improve: Patching is an ongoing process. After each cycle, validate the changes and refine your strategy. This helps ensure that your approach remains effective and minimizes disruptions.
Patch Now, Next, or Never?
Even with a structured approach like The Virtuous Loop, not every vulnerability demands immediate action. In OT environments, where uptime is critical, a more nuanced approach is needed. The Patch Now, Next, or Never? framework helps organizations make informed decisions by weighing security risks against operational impact.
✅ Patch Now: When a vulnerability is actively being exploited or poses an immediate, high risk to your environment, delaying isn’t an option. This is your fire alarm scenario, like fixing a major leak before it floods the system.
- The vulnerability is actively being exploited in the wild.
- CVSS score indicates critical severity (e.g., high CVSS score with low attack complexity and remote exploitability).
- The risk of attack outweighs downtime concerns.
- It affects a critical system with no available mitigations or compensating controls.
⏳ Patch Next: Some vulnerabilities present a risk but don’t require immediate action. These can be scheduled for the next maintenance window, reducing disruption while still addressing the issue before it escalates.
- The vulnerability is not actively being exploited but has known proof-of-concept exploits.
- CVSS score indicates medium-to-high severity but with mitigating factors (e.g., requires local access or complex attack conditions).
- The system is lower risk or has compensating controls in place.
- Patching requires coordination with multiple teams or planned downtime.
- Alternative mitigations (e.g., firewall rules, access controls) exist to reduce immediate exposure.
❌ Patch Never: In some cases, the operational risks of applying a patch may outweigh the security benefits, making it impractical to proceed. Legacy systems, vendor restrictions, or operational constraints may make traditional patching impractical. Instead, compensating controls, such as network segmentation or intrusion prevention systems, must be put in place to mitigate the risk.
- CVSS score indicates low severity or minimal exploitability (e.g., requires physical access or highly complex attack).
- The affected system is a legacy asset that can’t be updated without significant operational impact.
- Vendor restrictions prevent patching.
- Patching fails validation, introducing the risk of operational failure, and alternative security measures are available.
Deciding whether to patch now, next, or never isn’t just about following a checklist. It requires continuous evaluation of threats, asset context and criticality, and operational constraints. The key is balancing security with business continuity, ensuring that risk is managed without unnecessary disruptions.
Demystifying Virtual Patching
In some situations, installing a traditional patch is not possible. This could be due to vendor restrictions, operational risks, or legacy systems that no longer receive updates. When patching is not an option, organizations often use mitigations, such as virtual patching as an alternative security measure.
Virtual patching adds a protective layer around vulnerable systems, shielding them from threats without modifying the underlying software. Instead, security controls such as intrusion prevention systems or firewalls monitor and block potential threats. This is like hiring a security guard to protect a building with a broken lock. The guard controls access and prevents unauthorized entry, even though the lock remains broken.
While virtual patching reduces risk, it is not a permanent fix. It does not eliminate the vulnerability, only shields it from exploitation. Relying on it for too long can leave systems exposed if attackers find ways to bypass protections. Virtual patching should be used strategically, as part of a broader security approach, rather than as a long-term replacement for proper patching.
Building a Strong OT Patching Strategy
A solid patching strategy is not just about security, it is about maintaining stability. A disorganized or reactive approach can lead to downtime, compliance gaps, or even greater security risks. Instead, organizations need to adopt a process that ensures vulnerabilities are addressed efficiently while keeping systems stable.
Key best practices include:
- Comprehensive asset visibility: A well-maintained inventory is essential for identifying vulnerabilities early. Without clear visibility, you risk overlooking potential threats.
- Configuration management: Ensuring patches align with system configurations and operational constraints is crucial. A well-managed configuration baseline helps determine vulnerability risk, patch applicability and reduces the risk of unintended disruptions.
- Patch validation and rollback strategies: Before deploying any patch, validate it in a controlled environment, with a defined testing strategy. And always have a rollback plan in case something goes wrong.
- Continuous monitoring and reporting: Track patching efforts, identify emerging vulnerabilities, and stay on top of compliance. Continuous monitoring helps refine your strategy over time and ensures that nothing slips through the cracks.
Managing the complexities of OT patching requires specialized expertise and the right tools. Foxguard simplifies the process by offering tailored solutions designed to meet the unique needs of OT environments. Our services include:
- Asset & Vulnerability Management: Gain comprehensive visibility into your security landscape, so you can proactively manage risks.
- Patch Intelligence & Acquisition: Receive curated, actionable patch reports and secure binaries tailored to your systems.
- Patch Distribution & Deployment: Automate patching and updates with best-in-class tools, ensuring a smooth and efficient process.
- Managed Services: Let us handle patch and vulnerability management, allowing you to focus on your core operations.
With the right strategy and support, vulnerability management transforms from a disruptive task to a seamless, integrated part of your operations, helping you stay secure and resilient without compromising efficiency.
Final Thoughts
Patching in OT is a calculated process that demands careful planning and consideration. Unlike IT, where patching tends to be a straightforward routine, OT systems require a balance between security, risk, and the need for uninterrupted operations. With a strategic framework like The Virtuous Loop, combined with best practices and expert guidance, organizations can make confident decisions on when to patch, when to delay, and when to take a different approach.
The landscape of cyber threats is relentless and ever evolving. So, as an organization, how will you choose to navigate the complexities of OT patching?
Frequently Asked Questions
Q: What sustainable strategies exist to maintain consistent patching cycles? There’s a lot of focus on patch process during focused efforts to improve, but how can the good work be kept up over time?
A: Maintaining a sustainable and consistent patching cycle requires the following key features.
- Governance
- Automated deployment
- Setting SLA’s and aligning with vendor release schedules
- Prioritization based on risk
- Monitoring via audits and alerts maintain compliance
- Processes refinement through reviews and threat intelligence
Q: What is virtual patching vs patch deployment for software?
A: Virtual patching and patch deployment serve the same goal of mitigating software vulnerabilities, but they work differently.
- Patch Deployment involves applying official vendor-released updates to fix security flaws in software. This is the preferred long-term solution but can be delayed due to, compatibility issues, or operational constraints.
- Virtual Patching is a temporary security measure that mitigates vulnerabilities without altering the software itself. It typically uses firewall rules, intrusion prevention systems, or web application firewalls to block exploit attempts. This is useful when official patches are unavailable, cannot be applied immediately, or when legacy systems are being used.
Q: What is the best way to validate new patches before a system wide update?
A: To validate new patches, first review vendor details and test deployment in a lab environment of like systems and validate functionality. Deploy patches in stages based on risk, ensuring a rollback plan is in place. Once validated, proceed with full deployment while continuing to monitor.
Q: Is the assumption that “patches” are vendor provided security fixes for computers with OS and applications. Do you include firmware updates as “patches” on other computerized devices (i.e. PLC’s, drives, etc.)
A: Firmware updates for industrial devices such as PLC’s are also released by the vendor. When compared to consumer operating systems it is more difficult to identify the correct update for the device. FGS offers a service that provides patches and firmware updates for industrial devices.
Q: Everyone wants to address and close the vulnerabilities identified on their systems immediately. However, that’s usually not realistic in an OT environment. Mitigation plans are usually necessary. What time frames do you consider to be an acceptable time frame to complete a Mitigation Plan to “plug” those vulnerabilities? 30 days? 90 days? 6 months?
A: In an OT environment, mitigation timelines depend on risk severity, system criticality, and operational constraints. Based on NEI guidance, the following time frames are generally acceptable:
- Critical (Actively Exploited, High-Risk) ≤30 days
- Immediate mitigations (network segmentation, disabling services) with a plan for full remediation.
- High (Serious Risk, No Immediate Exploit) ≤90 days
- Controlled patch deployment, enhanced monitoring, or access restrictions.
- Medium (Moderate Risk, Limited Exploitability) ≤6 months
- Address during scheduled maintenance with compensating controls in place.
- Low (Minimal Risk, No Immediate Threat) ≤12 months
- Best-effort patching or mitigations as part of routine updates.
Key Considerations: Downtime constraints, regulatory requirements, vendor patch availability, and compensating controls (e.g., segmentation, monitoring).
Q: What are the best security practices for improving the security of OT machines that have been running 24/7 without a reboot for years across multiple sites? Besides using a maintenance window, what additional measures should be considered to mitigate risks?
A: Enhancing OT security for 24/7 systems requires risk mitigation without disruption. Key practices beyond maintenance windows include:
- Network Segmentation & Access Control – Isolate critical assets (IEC 62443), restrict traffic with firewalls/VLANs, and enforce Zero Trust.
- Application Whitelisting & Hardening – Allow only approved applications, disable unused services/ports, and enforce read-only configurations.
- Endpoint Protection & Monitoring – Deploy passive IDS/IPS, enable host-based logging, and use OT-specific threat detection.
- Secure Remote Access – Require MFA, use jump hosts, and enforce strict VPN controls.
- Patch & Virtual Patching – Apply firewall rules, IPS policies, and test patches in a sandbox before deployment.
- Backup & Disaster Recovery – Maintain air-gapped backups, golden images, and a tested incident response plan.
- Physical Security & Insider Threats – Restrict access, monitor USB connections, and enforce security training.