MAINTAIN THE FLOW OF YOUR PIPELINE AND SUPPLY CHAIN
Foxguard’s products and services address SD Pipeline 2021-02D
The Department of Homeland Security (DHS) Transportation Security Administration (TSA) has issued Security Directives (SDs) for pipeline owners/operators. SD 2021-02D is the “Pipeline Cybersecurity Mitigation Actions, Contingency Planning, and Testing” mandate from the TSA. This fourth revision, published in 2023, applies to owners/operators of TSA-designated hazardous liquid and natural gas pipelines or liquified natural gas facilities.
MANDATES
Similar to other TSA cybersecurity directives, SD2021-02D mandates the following:
- Designate a Cybersecurity Coordinator.
- Report cybersecurity incidents to the U.S. Cybersecurity and Infrastructure Security Agency (CISA).
- Conduct a cybersecurity vulnerability assessment.
In the 2023 revision, pipeline owners and operators must:
- Establish and implement a TSA-approved Cybersecurity Implementation Plan (CIP).
- Develop and maintain an up-to-date Cybersecurity Incident Response Plan (CIRP) that minimizes the risk of operational disruption or decreased capacity in a cybersecurity incident.
- Test at least two CIRP objectives annually.
- Establish a Cybersecurity Assessment Plan (CAP) and submit an annual update for approval that shows regular, proactive assessments and resolutions of vulnerabilities against results from the previous year. TSA requires testing of 100% of the owner/operator’s security measures every three years.
FOXGUARD OFFERS CYBERSECURITY VULNERABILITY ASSESSMENT SERVICES
Vulnerability assessment is the ongoing process of finding weaknesses in your security controls, prioritizing them, and deploying compensating controls like patching. CISA publishes annual reports summarizing their vulnerability assessments, the most common attack pathways, and mitigation and remediation recommendations Risk and Vulnerability Assessments | CISA.
What We Do
With a thorough vulnerability assessment from Foxguard, you’ll meet the vulnerability assessment requirement of SD 1582-21-01A and SD 1580-21-01A, as appropriate.
What You Achieve
Besides meeting requirements for vulnerability assessments, our services help TSA-designated pipelines to:
- Make decisions about controls.
- Update policies and procedures.
- Improve threat detection.
- Develop mitigation strategies.
RANSOMWARE ATTACKS ON OIL
The Risk to the O&G Industry Is Increasing
Threat actors frequently target the oil and gas (O&G) industry because of its political and economic importance and highly volatile processes. The O&G industry faces even greater vulnerability today as more operational technology (OT) equipment comes online. Moreover, fallout from an attack can range from death to interruptions in service, lawsuits, and fines.
EUROPEAN ATTACKS
In 2022, ransomware attacked Oiltanking GmbH, a German oil distributor. The attack paralyzed the automatic tank loading/unloading system. This pushed the company to find alternative charging points. In 2022 hackers attacked several European oil transport and storage companies, such as SEA-TANK in Belgium and Evos in the Netherlands.
U.S. ATTACKS
The United States is not immune to these attacks. In 2021, hackers entered the networks of Colonial Pipeline, the largest pipeline system for refined oil products in the United States. The hackers went through an unused VPN account. This hack opened the path for a ransomware attack that caused the shutdown of the entire pipeline, disrupting the flow of 2.5 million barrels of fuel per day.
Within two hours, the threat actors stole 100GB of sensitive company data, and Colonial Pipeline paid a $4.4 million ransom to obtain the decryption code. Subsequently, Colonial Pipeline was ordered to pay almost $1 million in fines for safety regulation violations.
WHAT ARE ADVANCED PERSISTENT THREATS?
Cybersecurity Is Vital To TSA-Designated Pipelines
COMPLIANCE IS MANDATED
Compliance with SD Pipeline 2021-02D is not optional. It’s a directive that owner/operators designated as critical must comply with.
DIGITIZATION IN ICS CREATES POTENTIAL ATTACK VECTORS
Although the ongoing IT/OT convergence and digitization in industrial control systems (ICS) offer numerous advantages, they also can create potential attack vectors for threat actors.Industrial control systems (ICS) present significant challenges when implementing an effective and efficient cybersecurity strategy for operational technology (OT). These are challenges that Foxguard has mastered.
VITAL TO PEOPLE’S LIVES AND THE ECONOMY
A third reason that cybersecurity measures are vital for pipelines is that O&G services are critical to people’s livelihoods and the economy.
Fourth, the threat is real.
Cybercriminals exploit the expanded IT/OT connectivity to infiltrate systems and introduce malware to disrupt operations in ICS OT environments, partners, and supply chains.
Want to know more about our products?
WE ARE
Your Cybersecurity Partner for O&G Operations
Foxguard serves as an extension of your team to solve the challenges that O&G operators face daily.
FOXGUARD ADDRESS THE ENTIRE O&G SUPPLY CHAIN
Our cybersecurity solutions apply to the O&G supply chain:
- Upstream, oil and gas exploration and production.
- Midstream, transportation and storage.
- Downstream, refining and marketing.
WE'LL SHOULDER THE BURDEN
We take on cybersecurity’s complex and tedious functions allowing you to focus on your core business. We will assess your security measures to improve your protection and maintain a strong defense. Cyber threats are constantly evolving. With Foxguard, you’ll stay ahead of cyber threat trends, so your infrastructure remains secure.
CYBERSECURITY GOVERNANCE CONSULTING SERVICES
Governance and Compliance Consulting Services
Foxguard’s cybersecurity governance consulting services help organizations establish a program of effective security measures to protect critical assets from cyber threats. These services assess the organization’s current security posture, identify critical gaps and vulnerabilities, and address them through remediation or documentation. The services include the following components:
- Vulnerability and Patch Management
- Objective, third-party risk assessment.
- Third-party vulnerability scan.
- Penetration testing.
- Security awareness training.
- Ongoing monitoring and support.
By partnering with Foxguard on cybersecurity governance consulting services, oil and gas companies proactively manage their cybersecurity risks and ensure the safety and security of their operations, employees, and customers.
POLICIES, STANDARDS, GUIDANCE, AND PROCEDURES PROGRAM AND DOCUMENTATION
Our governance and compliance experts help develop policies, procedures, and protocols that adhere to industry standards and regulatory requirements.
CYBERSECURITY PLAN AND PROJECT MANAGEMENT
If you wish, we’ll manage your cybersecurity remotely or onsite. It’s up to you. We’ll also provide project management to ensure project oversight. Of course, we’ll collaborate and consult with your key stakeholders throughout the process.
OUR STRATEGIC PARTNERSHIPS
We implement the optimal cyber controls safely and reliably for your organization
We work with strategic partners to implement the optimal cyber controls safely and reliably for your organization.
TECHNOLOGY AND SYSTEMS INTEGRATION
When your pipeline operation has unique technology and systems integration needs, we address these. Some technology and systems integration solutions for cybersecurity in O&G include:
- Technology stack evaluation and consulting
- Certified technology expertise and reseller agreements
- Network architecture & engineering services
COMPLETE PROGRAM AND SYSTEM INTEGRATION CAPABILITIES
Our programmatic solutions enable us to be a one-stop shop for your O&G pipeline vulnerability and patch management. We judiciously build, implement, and maintain cost-effective cybersecurity plans and systems that address all you need and only what you need. You’ll have the highest level of cybersecurity while meeting budget requirements.
SIX REASONS TO TRUST FOXGUARD
6 Reasons for Customers to Tap Foxguard
Foxguard is committed to evaluating your risk and developing solutions for your assets and environment. OT presents unique challenges when implementing an effective and efficient cybersecurity strategy, so we collaborate with you to learn your specific OT environment.
AGILITY
We stay agile to implement solutions for mature ICS systems, providing the best cybersecurity in a constantly changing threat environment.

INTEGRITY
We offer high-integrity processes and procedures to securely manage your cyber protections, so employees and civilians stay safe.

BUDGETS
We provide cost-effective programmatic solutions—not generic, one-size-fits-all services. Therefore, your assets are protected with the highest level of cybersecurity while meeting budget requirements.

EXPERTISE
We are Certified Information Security Professionals (CIISPs) with engineering/networking capabilities to do the job. We have a proven record of security in critical infrastructure.

COMPLIANCE
We offer programmatic assessment and program development to support standards and frameworks, such as TSA, NERC CIP, NIST CSF, and API 1164 regulatory requirements.

EXPERIENCE
Foxguard is a cybersecurity leader with over 30 years in cybersecurity, compliance, and industrial computing solutions. Foxguard implements cybersecurity solutions in highly-regulated critical infrastructure.
PATCH MANAGEMENT
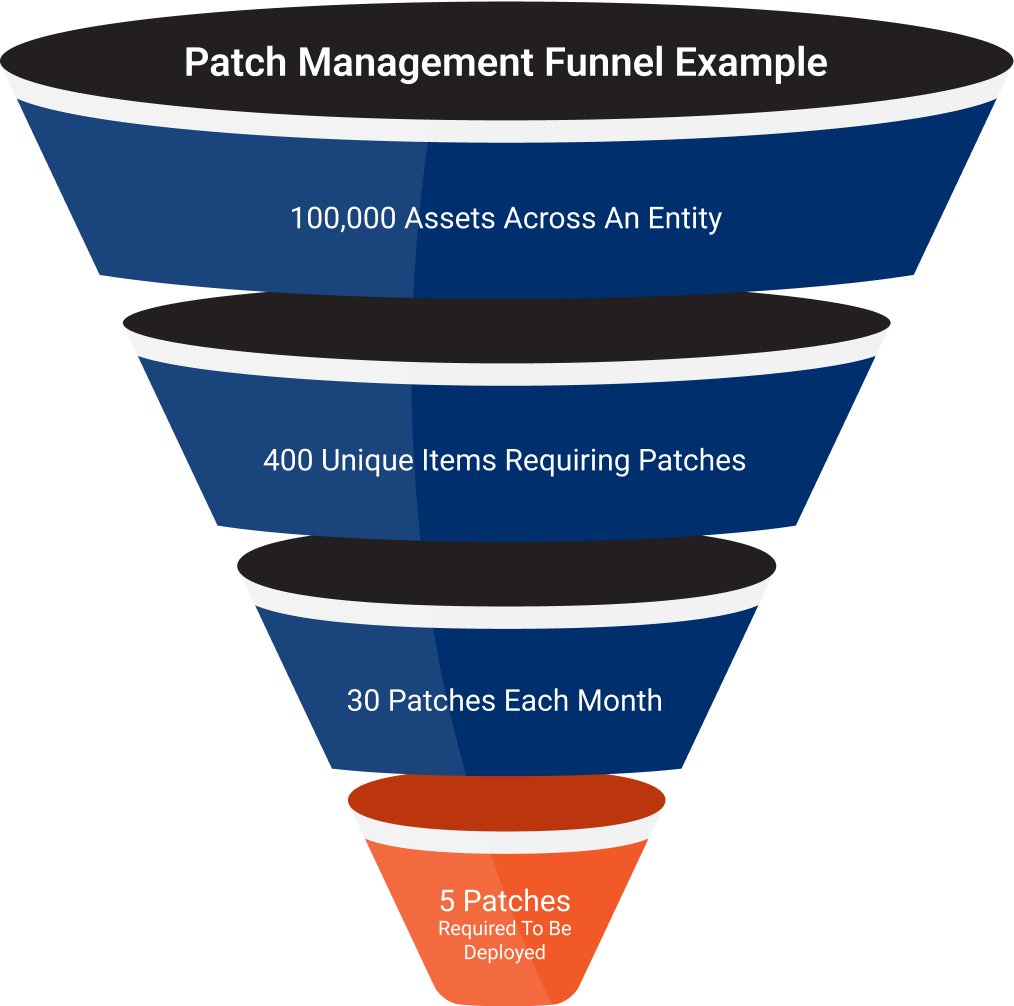
Our Patch Management Funnel Removes the Noise
We can remove the noise of your patch management program by filtering your hundreds of thousands assets down to hundreds of unique items (UI) requiring patches. In the funnel example, we show 100,000 assets filtered to 400 UIs. Those 400 UIs will typically only require 30 to 50 patches every 35 days. You’ll deploy a percentage of those patches depending on your mitigation techniques.
We Manage the Burden, So You Don’t Have To
Our program manages your asset list so that you can remain compliant and remove the burden of:
- Calling each vendor.
- Manually documenting patch vs. no patch.
- Collecting evidence.
- Tracking each asset. (We publish your unique patch report.)
- Acquiring authentic patches and ensuring the integrity of each one.
- Testing and validating patches before deployment.
We facilitate efficient patch management so you can readily deploy secure, validated patches on your schedule.
OUR CLIENTS SAY IT THE BEST

