NUCLEAR POWER PLANT SYSTEMS
Protecting Nuclear Power Plant Systems From Cyber Attacks For 12+ Years
At Foxguard, we design, manufacture, and integrate cyber security and industrial computing solutions to comply with the U.S. Nuclear Regulatory Commission’s (NRC) guidance for critical infrastructure. This includes NRC-endorsed NEI 08-09, NEI 13-10, and NEI 10-04 to meet 10 CFR 73.54. We have delivered cyber security programs to protect U.S. and global nuclear power plant systems from cyber-attacks for more than 12 years.
INDUSTRIES AND COMPLIANCE
Protecting ICS, OT, and IT for Nuclear Power Facilities
Protecting industrial control systems (ICS), operational technology (OT), and Information technology (IT) for nuclear power plants requires a strong defense against cyber intrusions and consistent adherence to regulatory requirements.
NUCLEAR REQUIREMENTS AND GUIDANCE
We Are Highly Experienced in Cybersecurity Requirements and Guidance for the Nuclear Power Industry
10 CFR 73.54: THE CYBER SECURITY RULE
Title 10 in the Code of Federal Regulations (CFR), Section 10 CFR 73.54,
requires the “Protection of digital computer and communication systems and networks.” It’s sometimes referred to as the Cyber Security Rule.
As a result of 10 CFR 73.54, nuclear utilities must take measures to protect computer and network assets from cyber-attacks.
RG 5.71: CYBER SECURITY PROGRAM FOR NUCLEAR FACILITIES
In response to 10 CFR 50.35 and 10 CFR 50.34(c), the NRC created Regulatory Guidance (RG) RG.571: “Cyber Security Program for Nuclear Facilities.” RG 5.71 applies to all NRC licensees.
Among other guidance, it addresses vulnerability scanning tools. It also
requires security controls for all critical digital assets (CDAs). To support uniform implementation of cyber security measures, the NRC also endorsed the Nuclear Energy Institute (NEI) guidance: NEI 08-09, NEI 13-10, and NEI 10-04.
NRC-Endorsed NEI Guidance
NEI 08-09
NEI 08-09 is “Cyber Security Plan for Nuclear Power Reactors.” This comprehensive guidance from NEI addresses 10 CFR 50.34(c) for “Physical Protection of Plants and Materials” and 10 CFR 73.54, the Cyber Security Rule.
Nuclear licensees must provide “high assurance” that digital computer and communication systems and networks are adequately protected.
CYBER SECURITY PLAN Security Plan
10 CFR 73.54 requires each nuclear facility licensee to submit a cyber security plan (CSP).
The CSP must describe how the licensee will fulfill cyber security and safety requirements. It also must account for site-specific conditions that impact implementation.
Additionally, the CSP must include measures for incident response and recovery from cyber-attacks. The licensee must detail the following:
- Maintain the capability for timely detection and response to cyber-attacks.
- Mitigate the consequences of cyber-attacks.
- Correct exploited vulnerabilities; and
- Restore affected systems, networks, and equipment affected by cyber-attacks.
Additionally, the CSP must demonstrate how the licensee will protect public health and safety in the event of a cyber-attack that results in radiological sabotage. This is to meet the requirements outlined in 10 CFR 50.34(c).
Our cyber security consultants are experienced in developing, implementing, and monitoring CSPs for nuclear power facilities.
DEFENSIVE ARCHITECTURE
Further, NEI 08-09 describes the need for a defensive architecture and a set of security controls based on the NIST SP 800-82, “Guide to Operational Technology (OT) Security Industrial Control Systems Security.” Learn more about our design architect and engineering capabilities in technology and systems integration for cyber security.
CYBER SECURITY ASSESSMENT TEAM
The Cyber Security Assessment Team (CSAT) includes individuals with expertise in information and digital technology, nuclear power plant operations, physical security, and emergency preparedness. Our cyber security consultants are experienced in working with CSAT teams. Foxguard has the people needed to round out your team.
ASSET INVENTORY
Identifying CDAs is part of NEI 08-09. We are experts in asset inventory management.
SECURITY CONTROLS, ACCOUNTABILITY, AND P&PS
NEI 08-09 also includes a set of security controls based on NIST SP 800-53, “Recommended Security Controls for Federal Information Systems.” Access controls, accountability, policies and procedures (P&Ps) are also required. Foxguard has the resources and experience to develop, write, and assist you with NEI-compliant P&Ps.
SYSTEM HARDENING
Further, NEI 08-09 guides system hardening, another Foxguard cyber security service.
NEI 13-10: CYBER SECURITY CONTROL ASSESSMENTS
Nuclear plants have thousands of CDAs and digital components, but not all are relevant to operational, safety, or security. NEI 13-10 is an effort to streamline the workload associated with the Cyber Security Assessment required by 10 CFR 73.54 (b)(1). This requirement builds on RG 5.71 and is outlined in NEI 08-09. It allows Licensees to group CDAs into four categories based on the consequences of a potential cyber-attack:
- Direct
- Emergency Planning (EP)
- Balance of Plant (BOP)
- Indirect
These are based on the importance of a CDA (Critical Digital Asset) to a plant’s safety, security, operations, and emergency planning requirements and are defined at length in NEI 13-10.
NEI 10-04: IDENTIFYING SYSTEMS AND ASSETS SUBJECT TO THE CYBER SECURITY RULE
NEI 10-04 is “Identifying Systems and Assets Subject to the Cyber Security Rule.” NEI 10-04 provides guidance for identifying digital computer and communication systems and networks subject to the requirements of 10 CFR 73.54. Foxguard can guide your compliance to NEI 10-04.
CSA N290.7(2021)
We also work with Canadian nuclear power plants, ensuring they are compliant with CSA N290.7(2021).

PROGRAMMATIC APPROACH
Our Programmatic Cyber Security Solutions for Nuclear Facilities
Threats, regulatory guidance, and plant digital systems are constantly changing. Foxguard can assist in cyber security procedure revisions to implement changes to regulatory guidance (i.e., future revisions to RG 5.71, NEI 08-09, 13-10, 10-04, NRC SFAQs). Foxguard can assist design engineering and/or the I&C vendor during conceptual design and detailed design to assure new designs comply with the plant specific cyber security plan, processes, and procedures. Foxguard has a programmatic approach to cyber security services for nuclear power plant systems. This approach helps to minimize the cost of ongoing plan-related cyber security activities. We can also provide cyber security consulting for plant design modifications and maintenance-related work.
NEI, NRC, NERC-CIP CYBER SECURITY SERVICES
Discover our Most Popular Services for Nuclear Power Plants
CYBER SECURITY PLANS (CSPS)
Our cyber security consultants can develop, implement, and provide ongoing operational support for your CSPs. By choosing Foxguard, you benefit from a seamless solution with a single source of accountability. With Foxguard, you can feel confident that:
- You have selected a partner with the expertise, resources, and tools to fully develop and implement your CSP.
- You are meeting security standards and cyber security regulatory requirements for Critical Systems and CDAs in the nuclear facilities sector.
CDA ASSESSMENTS
Foxguard offers the optimal mix of plant engineering, regulatory proficiency, and cyber expertise. We combine that expertise with a pragmatic approach to assess your CDAs to identify and mitigate security gaps, whether technical, programmatic, or organizational. Learn more about our asset inventory management and patch management solutions.
CONTINUOUS MONITORING AND THREAT DETECTION
The Foxguard team has a proven record of deploying security applications that provide the highest return with the lowest plant impact. Our Security Engineering team can help choose and integrate Products for backup and recovery, malicious software removal, log aggregation, SIEM/SOAR, and Network Anomaly detection. See our vulnerability management consulting services and patch management solutions.
Want to know more about our products
PERIODICITY PROGRAMS AND PERIODIC ACTIVITIES
Support You Need, Only When You Need It
Rather than increasing headcount for periodic activities, you can rely on Foxguard for the support you need—only when needed. As a leading cyber security provider, we provide specialized skills to maintain your cyber security plan. Rest assured, your cyber security is being managed with excellence and efficiency by Foxguard. The Foxguard team will provide cyber security support to ensure you keep up with:
- The evolving threat landscape.
- Revisions to regulatory guidance.
- Changes to plant instrumentation and control (I&C) systems to address obsolescence and plant life extension.
The advantages of using Foxguard for periodic cyber security tasks vs. performing them yourself are:
- Lower costs due to economies of scale.
- Experience across US and International Nuclear Power Plants for risk informed and optimized techniques.
- Broad experience outside Nuclear to draw from that can lead to innovations in completing periodic tasks.
Learn more about our Nuclear Periodicity Services.
REGULATORY AFFAIRS SUPPORT
Help Ensure Positive Outcomes
Foxguard can provide industry-recognized regulatory affairs support to ensure the successful outcome of NRC cyber security interactions and inspections. Our regulatory compliance support can include assessments, effective analysis, and simulated inspections.
PERIODIC ASSESSMENT AND EFFECTIVENESS ANALYSIS
We can periodically assess and analyze the effectiveness of your implementation efforts according to a defined regulatory and inspection support model.
PRE-NRC INSPECTIONS
We will perform a pre-NRC inspection to identify potential gaps and assess regulatory compliance, reviewing justifications supporting alternate controls.
Want to know more about our products?
NUCLEAR PATCH MANAGEMENT SOLUTIONS
Discover Our Full Suite of Patch Management Solutions
In addition to our programmatic cyber security services, Foxguard provides a full suite of patch management solutions that comply with NRC requirements and can address the cyber security needs of nuclear power plants.
IDENTIFYING YOUR ASSETS AND DETERMINING YOUR CDAS
Banish uncertainty. Creating/maintaining an asset inventory is an important prerequisite to determining asset criticality. We can help identify and inventory each of your OT assets with our exclusive set of tools and expert team. After Foxguard conducts an asset inventory, you can classify your assets into the following categories:
- Safety
- Important to Safety
- Physical security functions
- Emergency preparedness, including offsite communications
- Balance of plant systems
Further, we will help you streamline your organizational assets.
For new nuclear plants or those changing their plant design, we will generate a detailed, normalized report with all your assets. This report will identify the manufacturer, product name, and version. We also anticipate future asset identification for those using emerging nuclear technologies, such as advanced reactors and small modular reactors.
PATCH VALIDATION PROGRAMS IN A CONTROLLED ENVIRONMENT
Test and Validate your patches. Deployment is critical when implementing patches to various assets across an organization.
We can validate your patches in a controlled environment before deployment or help you build a validation lab to test patches before releasing them into an active environment. You can choose from multiple options for running your lab:
Foxguard builds and runs your validation lab for you. Ensuring all patches are functioning properly before deployment.
Foxguard co-manages your validation lab by providing your team with guidelines to follow and checkpoints before deployment.
Foxguard trains and equips your team to run your validation lab independently.
PATCH AVAILABILITY REPORT (PAR)
Know your weaknesses. We create a recurring human and machine-readable report detailing vulnerabilities of your assets and the necessary patches. It’s all done without ever touching your equipment. Our PAR report is delivered monthly to your security management team so you can maintain or work toward regulatory compliance.
PATCH BINARY ACQUISITION (PBA)
Trust your solutions. Foxguard has a secure supply chain from source vendors to the point of application. Foxguard’s tools verify the source of every patch and ensure they are unchanged before deploying them to your OT environment. This ensures that each patch remains uncorrupted and precisely as the original vendor intended.
PATCH APPLICABILITY
Deploy the right solutions. We take a hands-on approach using the Patch Availability Report to determine the appropriate patch source including security/non-security designation and end of support (EOS).
SENTRIGARD™ PATCH DEPLOYMENT
Hardwire your success. We install Sentrigard Patch onsite to encrypt and
deliver patches securely. This unique solution complies with regulatory
standards, such as NERC CIP.
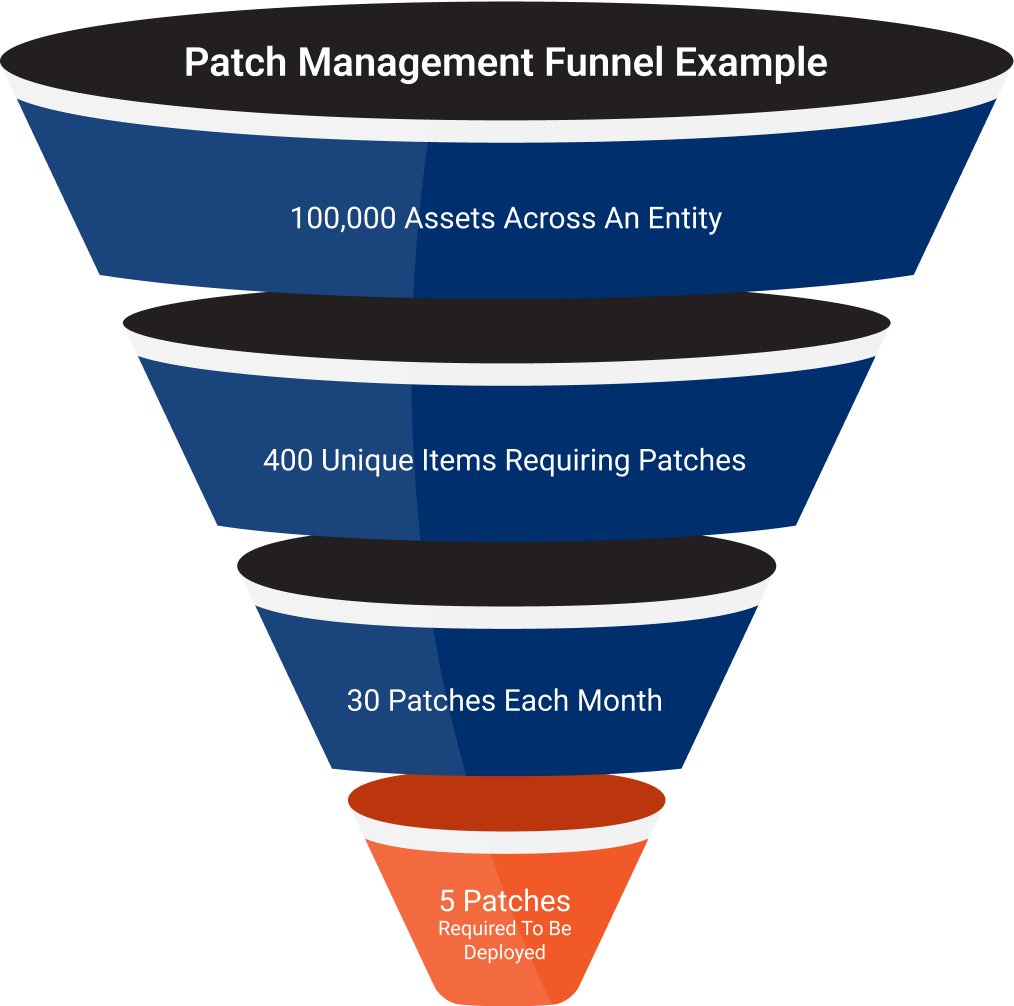
PATCH MANAGEMENT SOLUTIONS
Our Patch Management Solutions Removes the Noise
We can remove the noise of your patch management program by filtering hundreds of thousands assets down to hundreds of unique items (UI) requiring patches. In the diagram, we show 100,000 assets filtered to 400 UIs. Those 400 UIs will typically only require 30 to 50 patches every 35 days. You will deploy a percentage of those patches depending on your mitigation techniques.
We Manage the Burden, So You Don’t Have To
Our program manages your asset list so that you can remain compliant and remove the burden of:
- Calling each vendor.
- Manually documenting patch vs. no patch.
- Collecting evidence.
- Tracking each asset; we publish your unique patch report.
- Acquiring authentic patches and ensuring the integrity of each one.
- Testing and validating patches before deployment.
We facilitate efficient patch management so you can readily deploy secure, validated patches on your schedule.
Want to know more about our products
NEI Cyber Security
A Slow Whirlwind of Changes
NRC’s cyber security requirements are constantly evolving based on the ever-changing nature of cyber threats. As a result, the regulatory frameworks that drive enhanced cyber protection are also moving targets.
As leaders in cyber security, Foxguard participates in the Nuclear Energy Institute (NEI) Cyber Security Task Force. This keeps us current on regulatory inspection outcomes, changes to existing regulations, and new cyber security regulations (10 CFR 73.110) for the existing fleet and for new advanced reactor designs and small modular reactors.
Our cyber security experience in the U.S. Nuclear industry includes supporting more than 12 utilities, 20 plants, and 33 units around the world with their cyber security programs.
NEI AND OTHER NUCLEAR CYBER SECURITY WITH FOXGUARD
With Foxguard, your Nuclear Power Plant can achieve the following

MAXIMIZE YOUR BUDGET
We can help reduce your operation and management budget with programmatic services. Rather than increasing headcount for periodic activities, you can rely on Foxguard for the support you need—only when needed.

RETAIN WORLD-CLASS TALENT
Cyber security skills are in high demand. It’s challenging to keep the best professionals in-house. Our specialized cyber security consultants have lower turnover rates and support the uniform implementation of cyber security measures.

ACCESS STRONG OT & IT EXPERTISE
Operations technology experience can be challenging to find. Foxguard has extensive experience with both OT and IT cyber security. We’re qualified engineers with deep expertise, degrees, and more than 15 unique cyber security certifications.
UNLOCK BROAD INFRASTRUCTURE EXPERIENCE
Our experts have experience in energy, nuclear energy, transportation, manufacturing, and DoD critical infrastructure sectors. Our broad understanding can lead to innovations in implementing your secure architecture.

COMPLY WITH YOUR INTERNAL PROCEDURES
We will ascertain and comply with your customized qualification procedures (QUALs), including Security Governance Initiative (SGI), Critical Group, and Cyber Security Specialist qualifications.

GET INTERNATIONAL AND U.S. NUCLEAR CYBER SECURITY EXPERIENCE
We have experience in United States and international nuclear plants, making us better qualified to apply solutions and meet regulatory requirements. We also provide cyber security services for Advanced Reactor plant designs.

PROTECTING NUCLEAR POWER PLANT SYSTEMS
Is your nuclear power plant achieving its highest level of cyber security?
The ever-changing nature of cyber threats requires systematic and continuous assessment and implementation. Using the Cyber Security Capability Maturity Model (C2M2), we test the maturity of your cyber security system. We move progressively to assess risk, execute solutions, and monitor results, providing certainty that your nuclear power plant is continuously operating with the highest levels of protection.

Foxguard® is a wholly owned subsidiary of Framatome, an international leader in nuclear energy.
OUR CLIENTS SAY IT THE BEST

