CRITICAL MANUFACTURING
NIST 800-53, NIST 800-171, NIST CSF, NIST 800-82, and NIST 1800-10 for CRITICAL MANUFACTURING
The National Institute of Standards and Technology (NIST) at the U.S. Department of Commerce catalogs and publishes a set of security controls and technical guidelines. Foxguard offers a range of solutions that incorporate the NIST Cybersecurity Framework (CSF), NIST 800-53, NIST 800-171, and NIST 1800-10 for critical manufacturing.
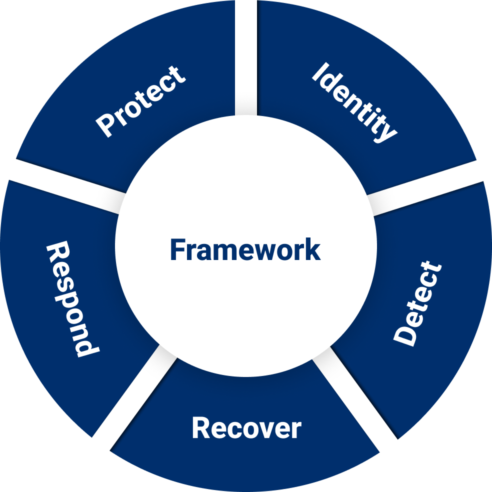
NIST CYBERSECURITY FRAMEWORK (CSF)
Identify and Respond to Cyber Risks
The NIST cybersecurity framework is a methodology to identify and respond to cyber risks, utilizing five significant steps:
- Identity
- Protect
- Detect
- Respond
- Recover
NIST 800-53
SECURITY AND PRIVACY CONTROLS FOR
INFORMATION SYSTEMS AND ORGANIZATIONS
NIST 800-53 rev 5 Crosswalk– Security and Privacy Controls for Information Systems and Organizations is a Privacy Framework. It encompasses “Security and Privacy Controls for Information Systems and Organizations.” SP 800-53 contains a catalog of controls for developing security policies and processes for organizations and information systems.
The document is a vital component of the NIST Risk Management Framework (RMF) and the Federal Information Security Modernization Act of 2014 (FISMA), formerly the Federal Information Security Management Act of 2002.
NIST designed the controls so applicable organizations can tailor them to their systems. The parameters apply to systems that store, process, or transmit federal information to protect the data’s Confidentiality, Integrity, and Availability (CIA).
NIST (SP) 1800-10: Cybersecurity for the Manufacturing Sector
Published in 2022, NIST SP 1800-10 is titled “Protecting Information and System Integrity in Industrial Control System Environments: Cybersecurity for the Manufacturing Sector.” The guidance suggests that critical manufacturers establish cybersecurity plans that begin by:
- Identifying their assets.
- Training their employees.
- Conducting a risk assessment.
From these three steps, manufacturers can apply NIST SP 1800-10 guidance and cybersecurity solutions to determine which tools, patches, and updates they can deploy to help mitigate their risk.
It provides examples that map to the NIST Cybersecurity Framework (CSF) and NIST SP 800-53 Rev. 5 (the foundation for NIST SP 800-171). It enables manufacturers to discover how commercial toolsets can be part of a comprehensive cybersecurity program.
NIST 800-171
PROTECTING CONTROLLED UNCLASSIFIED
INFORMATION IN NONFEDERAL SYSTEMS AND
ORGANIZATIONS
NIST SP 800-171 rev. 2 is “Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations.” (NIST released a draft of 800-171 revision 3 in May 2023.)
The publication sets out confidentiality-oriented controls required for all components of nonfederal information systems that process, store, or transmit controlled unclassified information (CUI).
It focuses on safeguarding CUI within nonfederal information systems and organizations, focusing on the confidentiality arena of the CIA triad.
Examples of CUI include controlled procurement and acquisition, and technical information. A complete list of CUI categories is identified in the National Archives CUI Registry. NIST SP 800-171 is also a requirement of DFARS 252.204.7012 for Federal contractors and subcontractors.
Foxguard’s Information Security Management System (ISMS) includes ISO 27001:2013 certified and compliance with all applicable NIST SP 800-171 controls.
NIST (SP) 800-82
NIST SP 800-82, Rev. 2, is “Guide to Industrial Control Systems (ICS) Security.” It provides guidance on how to secure ICS, including supervisory control and data acquisition (SCADA) systems, distributed control systems (DCS) and other control system configurations, such as programmable logic controllers (PLC). Rev. 3 is in draft format. It will be renamed “Guide to Operational Technology (OT) Security.”
Protecting Critical Infrastructure
Implementing NIST security controls and technical guidelines can enable any business to reduce its cyber-attack risk. Foxguard specializes in protecting the IT and OT of industrial control systems in critical infrastructure sectors. NIST special publications (SPs) also form the foundation for cybersecurity guidance for many critical infrastructure sectors subject to other regulations and guidance. Besides NIST and NIST CSF, our team has extensive industrial control systems knowledge and experience to protect critical infrastructure sectors with unique compliance requirements and guidelines:
- Critical Manufacturing (NIST 1800-10)
- Bulk Electric System (BES) (NERC CIP Guidelines)
- Nuclear Power Plants (NEI Cybersecurity Compliance)
- Rail Cybersecurity (TSA Railroad Cybersecurity)
- Gas and Oil Pipelines (TSA Pipeline Cybersecurity)
Want to know more about our products
THE THREAT FOR MANUFACTURERS IS REAL
Ransomware and Cyber-Attacks Continue To Be One Of The Biggest Concerns For Manufacturers Worldwide
THE MOST ATTACKED INDUSTRY
According to a 2023 threat intelligence report, manufacturing remains the most attacked industry worldwide, an inauspicious rank it has held for two years.
MANUFACTURING: MOST ATTACKS OF ALL OPERATIONAL TECHNOLOGY
Additionally, manufacturers were first among threats to operational technology (OT) and industrial control systems (ICSs). Among this group, manufacturers represented 58% of those targeted. The energy ICS was the second-most targeted OT in ICS, representing 17% of attacks.
Popular schemes include backdoor attacks, ransomware, phishing, and exploiting public-facing applications. Knowing manufacturing’s intolerance for downtime, threat actors favored ransomware. The results included extortion (32% of cases), data theft (19%), and data leaks (16%).
NIST reports that small and medium-size manufacturers (SMMs) are particular targets for cyber-attacks. It proposes that these organizations do not have access to the security of larger organizations but have more digital assets than individual consumers.
6 REASONS TO TRUST FOXGUARD
6 Reasons Critical Manufacturing Can Trust Foxguard’s Cybersecurity
As OT and IT converge, protecting operations has become more complex. However, Foxguard has mastered OT cybersecurity in industrial control sectors. Here are six reasons you can trust Foxguard with your cybersecurity protection.

SEAMLESSLY BRIDGE
THE IT/OT GAP
We’re experts in bridging the IT and OT gap for industrial control systems for critical manufacturing and others in the critical infrastructure sector.

ACCESS COMPLIANCE EXPERTS
Our team has extensive knowledge of NIST CSF, NIST 1800-10, and other cybersecurity guidelines. We can work with you to review your current program or help you create a new one that better addresses your security concerns.

AVOID THE COOKIE-CUTTER APPROACH
Rather than imposing a premade solution onto your organization, Foxguard develops “built-for-security” programs that:
- Address your organization’s unique challenges.
- Integrate with your current business operations.
- Meet you where you are in your cybersecurity, computing, or digitization journey.

WORK WITH A SINGLE-SOURCE
Wherever you are in cybersecurity, compliance, or digitization journey, we offer a wide range of built-for-security solutions.
- Asset Inventory Management
- Vulnerability Management and Patch Management
- Systems Integration
- Cybersecurity Consulting and Control Systems Hardening

THE THREAT IS REAL
In October 2020, the Cybersecurity and Infrastructure Security Agency (CISA) estimated that U.S. companies lost $394,000 to $19.9 million per cyberattack. In 2023, IBM reported that the average cost of a single cybersecurity data breach was $4.45 million—a 15% increase from 2020. Lax compliance is not an option. See sidebar: The Threat for Manufacturing Is Real.
WE’RE NIMBLE. AND RELENTLESS
Cybersecurity is never a “one-and-done.” The threats—both foreign and domestic—are continuous. Bad actors are relentless. So are we. We’re known for our readiness to quickly change directions and meet challenges head-on. We remain hypervigilant, tenacious, and flexible.
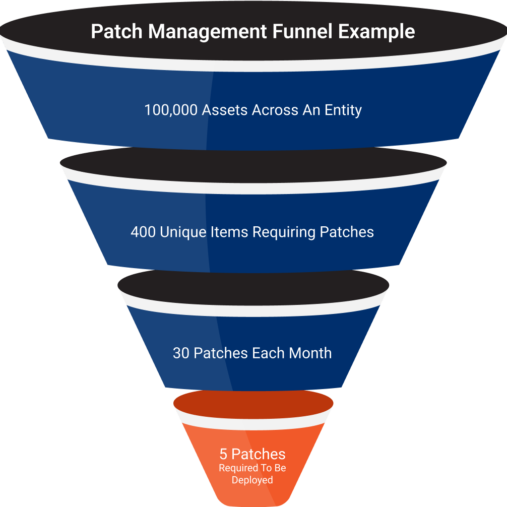
PATCH MANAGEMENT
Our Patch Management Funnel Removes the Noise
We can remove the noise of your patch management program by filtering your hundreds of thousands assets down to hundreds of unique items (UI) requiring patches. In the funnel example, we show 100,000 assets filtered to 400 UIs. Those 400 UIs will typically only require 30 to 50 patches every 35 days. You’ll deploy a percentage of those patches depending on your mitigation techniques.
We Manage the Burden, So You Don’t Have To
Our program manages your asset list so that you can remain compliant and remove the burden of:
Calling each vendor.
- Manually documenting patch vs. no patch.
- Collecting evidence.
- Tracking each asset. (We publish your unique patch report.)
- Acquiring authentic patches and ensuring the integrity of each one.
- Testing and validating patches before deployment.
We facilitate efficient patch management so you can readily deploy secure, validated patches on your schedule.
OUR CLIENTS SAY IT THE BEST

